Home Depot to Pay $27 25m in Latest Data Breach Settlement
Table of Content
- Chegg Faces Federal Trade Commission Lawsuit Over 2018 Breach
- Data Breach to Stanley Street Treatment and Resources Affects 45 Thousand People
- Data Breach of Healthcare Management Solutions, LLC Affects Half-a-Million People
- Wings Financial Services Claims Over 240 Thousand Victims in Massive Data Breach
- When Was the Home Depot Data Breach?
- Machine ID Management and Digital Transformation: Building a Secure Future
Your Wi-Fi network is another handy access point that hackers use to infiltrate your computers, steal your identity, and grab your personal details. Recently, it suffered a data breach that revealed the personal information of over 2. During the second quarter of 2022, the world as a whole has seen 52 million reported data breaches, which is down by 56% from the previous quarter.
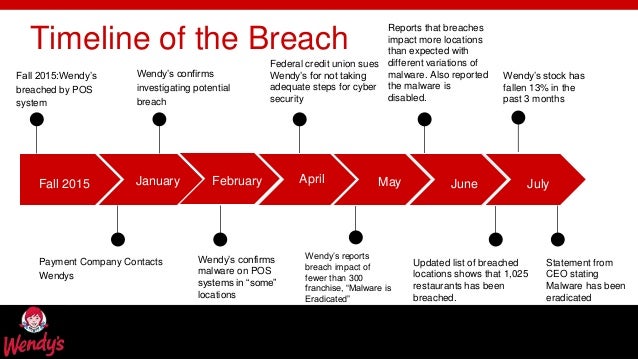
Launched as a project for U.S. stores in January 2013, the project will be completed ahead of the payment industry's deadline. /PRNewswire/ -- The Home Depot®, the world's largest home improvement retailer, today disclosed additional findings related to the recent breach of its payment data systems. The findings are the result of weeks of investigation by The Home Depot, in cooperation with law enforcement and the company's third-party IT security experts. If the cards currently being sold by criminals are in fact the cards stolen from Home Depot, then the breach likely exposed the customer's name, card number, and expiration date. Moreover, because all U.S. stores were being targeted, the criminals are able to split the card data into geographic lots, sorted by state and ZIP code. Keystone Health is a Pennsylvania-based healthcare system that employs over 500 people.
Chegg Faces Federal Trade Commission Lawsuit Over 2018 Breach
If you are one of the millions who have been affected by a data breach, or if you want to protect yourself, check out our top-rated identity theft protection companies. In our next article, we will discuss how chip-in-cards work and other alternative payments and why you should use them. The Target breach lasted roughly three weeks, but it exposed some 40 million debit and credit cards because hackers switched on their card-stealing malware during the busiest shopping season of the year. Prior to the Home Depot breach, the record for the largest retail card breach went to TJX, which lost some 45.6 million cards. Last year, the retailer also agreed to hire a chief information security officer , and said that it now applies enhanced encryption to payment card data. As reported by both The New York Times and Bloomberg’s BusinessWeek, Home Depot was repeatedly warned by its own IT security personnel about its poor and outdated IT security since 2008.
Krebs on Security reports that the company "may be the source of a massive new batch of stolen credit and debit cards" hitting the digital black market. Home Depot isn’t alone in blaming the supply chain for their breach. In 2015, Target agreed to pay $10 million in a settlement over a data breach it suffered in 2013 that affected 40 million cards. In that case, the criminals used compromised HVAC vendor credentials. The 2014 incident, which is the largest point-of-sale heist of all time, as well as the biggest credit-card compromise ever seen, affected 56 million different pieces of plastic. Now, banks that file valid claims will get $2 per compromised payment card without having to prove their losses, even if they have received compensation from another source.
Data Breach to Stanley Street Treatment and Resources Affects 45 Thousand People
The company believes it will be reimbursed $27 million thanks to its insurance coverage. Last month, Target announced that its breach cost the company $148 million, more than twice the amount Home Depot is estimating. If a company has a “Visit Site” and/or phone number next to its name, this indicates that we receive compensation from the company in exchange for referring prospective customers to them. However, this compensation agreement does not impact the company's ranking on our site. 100% of a company's ranking on BestCompany.com is determined by the reviews of its consumers.
It delivers software to governmental agencies to enable them to help veterans receive benefits from theU.S. With razor-slim margins, we must use every tool available to us to do more with fewer developers. When I decided that our company should switch to using functional languages, I didn’t want to put my developers through the same nightmare. So, I started building a curriculum for them to use, which became the basis for a book intended to help developers transition into functional programmers. Inmy book, I provide guidance for obtaining proficiency in a functional language called PureScript, which stole all the great aspects of Haskell and improved on many of its shortcomings.
Data Breach of Healthcare Management Solutions, LLC Affects Half-a-Million People
A Life Senior Member of the IEEE, Charette was a recipient of the IEEE Computer Society’s Golden Core Award in 2008. To tell you the truth, every time I read or hear a company or government agency claim in a press release that, “We take your security seriously,” in the wake of some security breach, I shake my head in disbelief. Why not just state honestly, “We promised to take your security seriously and we obviously failed to take it seriously enough.
From worldwide companies like SHEIN and Intel to smaller, less heard-of companies like iDealwine, there have been tons of hacks and leaks over the year. Unethical, or black hat, hackers have very little qualms against who they'll hack. Often, they'll go with either the easiest target or the most rewarding one, as most criminals do.
Only by adopting them will you get the many benefits that I’ve outlined here. Unlike most languages, functional programming languages are deeply rooted in mathematics. It’s this lineage in the highly disciplined field of mathematics that gives functional languages their biggest advantages. Software developers need to be extremely disciplined to avoid such pitfalls, and sometimes they don’t take adequate precautions. The architects of structured programming knew this to be true for GOTO statements and left developers no escape hatch. To guarantee the improvements in clarity that GOTO-free code promised, they knew that they’d have to eliminate it entirely from their structured-programming languages.
We’re sorry and we will be better prepared from now on.” Alas, that level of candor is probably much too much to ask. Further, investors have figured that Target’s breachcostthe company some $150 million, excluding the $90 million in insurance reimbursements—a sum the company could ill afford given its ongoing retail difficulties. A similar sum may dent Home Depot’s bottom line, but the company is better placed financially to absorb the damage.
While the company did eventually decide to upgrade its payment security systems, the implementation effort didn’t get started until April, the same month as the breach. In addition, the papers report, Home Depot seemed to have weak security monitoring of its payment system, even though company management knew it was highly vulnerable to attack. In fact, it wasn’t until 8 September that Home Depot confirmed that it had in fact suffered a breach.
However, sources close to the investigation have stated that a variant of the malware used against Target was discovered on the Home Depot network. First, seniors often have a lot of money in the bank from a life of working hard and saving. The North Face is an outdoor apparel company owned by VF Corporation.
CommonSpirit Health is the parent company for over 140 hospitals. It was the second largest nonprofit healthcare system in the U.S. in 2022 and the most prominent Catholic hospital chain in the U.S. as of 2019. Brute force attacks on computer systems are an effective means of entry for ransomware theft.
Comments
Post a Comment